NIST SP 800-37, the Risk Management Framework: A Guide in Plain English

NIST Special Publication (SP) 800-37, titled “Risk Management Framework for Information Systems and Organizations: A System Life Cycle Approach for Security and Privacy” is commonly referred to by its acronym, the RMF. It is a tool for helping organizations implement a holistic approach to designing systems with security and privacy at their core. By utilizing the RMF, agencies can achieve compliance objectives, such as, a continuous Authority to Operate (cATO) or FedRAMP certification.
Anchore has developed secure software supply chain systems that have helped numerous agencies achieve these compliance objectives. Across these engagements, Anchore has developed significant expertise in how to meet the requirements of these frameworks in the least burdensome way. In this guide, we will break down the RMF to help explain its goals and show how Anchore can help meet these goals.
What is NIST 800-37?
NIST SP 800-37, aka the Risk Management Framework (RMF), is a methodology for building a risk management program. It isn’t a ready-made risk management program but a framework for designing a program that will custom fit a specific organization. By utilizing the framework an organization can create a highly effective information security and privacy practice.
The RMF was developed by the Joint Task Force Transformation Initiative Working Group. It is specifically designed to modernize the security and privacy practices of federal agencies in response to the reality that the previous standards were falling behind. In a report by the Defense Science Board, there is a quote that drives this home,
The cyber threat to U.S. critical infrastructure is outpacing efforts to reduce pervasive vulnerabilities, so that for the next decade at least the United States must lean significantly on deterrence to address the cyber threat posed by the most capable U.S. adversaries. It is clear that a more proactive and systematic approach to U.S. cyber deterrence is urgently needed…
For most agencies or federal service integrators (FSIs) the most important takeaway from the RMF is that the framework will help you achieve compliance objectives faster and more efficiently than previous recommendations.
NIST 800-37 Revisions
NIST 800-37 has two revisions, with the first published in February 2010 and the other in December 2018.
NIST 800-37 Rev 1 Summary
NIST Special Publication 800-37 Revision 1, titled “Guide for Applying the Risk Management Framework to Federal Information Systems: A Security Life Cycle Approach” was published in 2010 with a minor update in 2014. It was meant as an evolution of a previous process called Certification and Accreditation (C&A). The 6-step Risk Management Framework (RMF) replaced the C&A process. To put this into context, the RMF was written when the majority of applications ran on mainframes in on-premise data centers and smart phones were two separate devices (a cell phone AND a PDA). The RMF was produced in order to achieve three key objectives:
- Modernize software security practices
- Improve monitoring processes
- Communicate key insights upwards in the organizational hierarchy
If you’d like to read the entire revision in full, you can find it here.
NIST 800-37 Rev 2 Summary
NIST Special Publication 800-37 Revision 2 titled, Risk Management Framework for Information Systems and Organizations: A System Life Cycle Approach for Security and Privacy was published in 2018. The landscape had changed significantly since 2010 and more modern documents had been created to make recommendations on how to design secure systems. This revision was meant to align the RMF with newer frameworks like the NIST Cybersecurity Framework and NIST SP 800-160.
Two larger updates to the content of the RMF was additional guidance on how to deal with software supply chain security and privacy into the systems designed within the framework. In the time since the first draft was published, the software landscape has shifted dramatically. Open source software became huge during that time frame. As open source software grew, it became more economical for adversaries to focus their attention on breaching the software supply chain rather than an organization directly. Revision 2 of the RMF addresses this and lays out specific guidance on how to address this.
On top of this, the RMF created an entirely new section dedicated to not only how to make systems secure but also how to ensure that the security properties also guarantee privacy. The global awareness of how much data large technology companies retain on their users has gradually ticked upward and became an important enough issue that the RMF now addresses it separately from security concerns.
Potentially the largest update to the RMF was the addition of one additional step in the framework. A preparatory step, aptly named, ‘PREPARE’ was added in order to help organizations know where to start when using the RMF to design a secure and private system.
The purpose of these updates were to simplify RMF execution, allow for innovative approaches to risk management and increase the level of automation when carrying out specific tasks.
If you’d like to read the entire revision in full, you can find it here.
The 7 Steps of the Risk Management Framework (RMF)
- Prepare for RMF Execution: Set up a framework and establish priorities at both organizational and system levels to manage security and privacy risks. This includes understanding the context and setting clear goals.
- Categorize System and Information: Analyze the system and the data it processes, stores, and transmits, and categorize them based on the potential impact if a loss occurs. This will help understand what needs to be protected and how crucial it is.
- Select and Tailor Controls: Choose a preliminary set of security measures for the system and customize them as necessary to manage risk down to an acceptable level, based on a risk assessment.
- Implement Controls: Put the selected controls into action and document how they are used within the system and its operational environment. This ensures that everyone understands how and why specific security measures are being applied.
- Assess Controls: Evaluate the implemented controls to confirm they’re set up correctly, functioning as intended, and achieving the desired outcomes in terms of meeting security and privacy needs.
- Authorize System or Controls: Approve the system or common controls for use based on a judgment that the remaining risk to the organization’s operations and assets, as well as to individuals, other organizations, and the nation, is acceptable.
- Monitor System and Controls: Continually keep an eye on the system and its controls. This includes assessing how effective the controls are, documenting any changes to the system or its operating environment, conducting risk assessments and impact analyses, and reporting on the security and privacy status of the system.
NIST 800-37 vs. NIST 800-53
NIST SP 800-37, or simply the RMF, is a framework for designing a risk management program. It is simplest to visualize via the graphic that accompanies it:
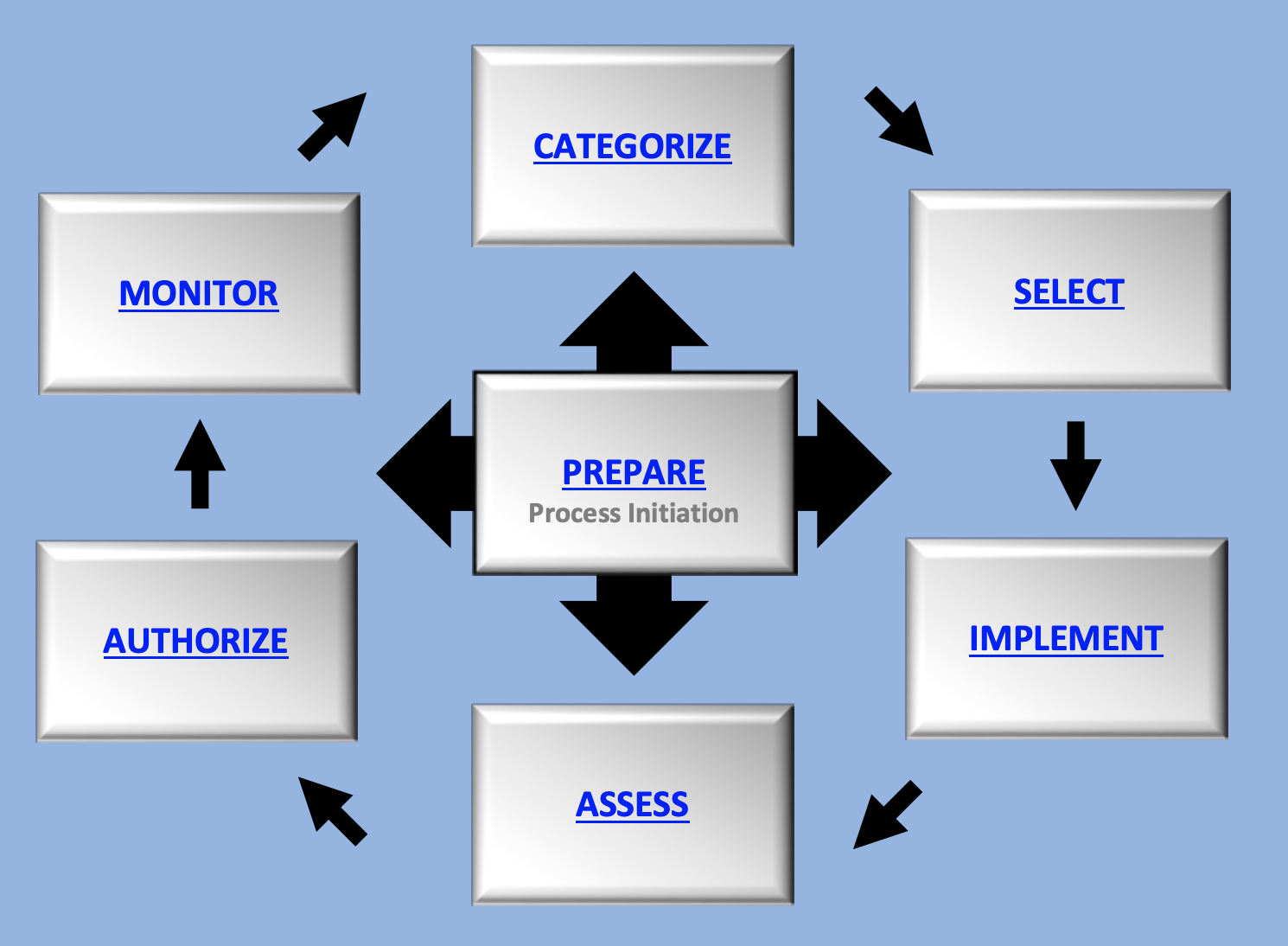
It is not meant to be a step-by-step guide on how to implement a system that has its risk fully managed. It is meant to be a program that guides agencies through the process of building their own risk management system.
NIST 800-53, on the other hand, is essentially a spreadsheet of specific controls that will meet different requirements of the RMF. It doesn’t go so far as recommending specific software to meet the control but it is much more prescriptive than the RMF.
Example of an RMF requirement
Task A-3: Control Assessments
Control assessments occur as early as practicable in the SDLC, preferably during the development phase. These types of assessments are referred to as developmental testing and evaluation, and validate that the controls are implemented correctly and are consistent with the established information security and privacy architectures. Developmental testing and evaluation activities include, for example, design and code reviews, regression testing, and application scanning. Deficiencies identified early in the SDLC can be resolved in a more cost-effective manner.
This task is meant to identify the purpose behind the control but not make any specific recommendations on how to achieve it. They provide some examples but purposefully keep the discussion high-level.
Example of NIST 800-53 control
RA-05 Vulnerability Monitoring and Scanning: RA-05a.[01]
Systems and hosted applications are monitored for vulnerabilities and when new vulnerabilities potentially affecting the system are identified and reported.
This is an example of a specific control that requires agencies to have a system in place that monitors their internal systems, or if their applications are hosted by a third-party, for vulnerabilities. When vulnerabilities are uncovered they need to be reported.
Manage & Automate NIST Compliance
The RMF and the accompanying NIST 800-53 document are very comprehensive and at the same time extraordinarily intimidating. NIST 800-53 catalogs more than 1000 different controls. Understanding this framework and the accompanying controls as well as getting all of these correct is easily a full-time job. That’s why automating the process with NIST compliance tools is so critical.
As agencies are determining whether to accomplish meeting these technology compliances they have to make the decision whether to DIY the entire process or work with 3rd party vendors that are experts in the process.
Anchore, in partnership with its many federal service integrator partners, has sheparded countless agencies through the process and provides a number of different features that not only make meeting controls simple but automate the continuous process of maintaining compliance in real-time.
The Anchore Enterprise platform was specifically designed to address the software security supply chain management of federal agencies. The platform is an automated system that manages a comprehensive inventory of the entire software supply chain, automatically scans all software packages for vulnerabilities and compliance and utilizes pre-built policy packs to report and ensure compliance standards are met.
If you’re interested to learn more about how Anchore can help your organization meet its compliance requirements, learn more by visiting our public sector page.